elering-9
Manage data logs
1. Description of the Use Case
1.1. Name of the Use Case
| ID | Area /Domain(s)/Zone(s) | Name of the Use Case |
|---|
| 1 | Access to data, Market for flexibilities, Operational planning and forecasting, Services related to end customers, Balance management, | elering-9 |
1.2. Version Management
| Version No. | Date | Name of author(s) | Changes | Approval status |
|---|
| 1 | 2018-06-01T00:00:00 | Kalle Kukk (Elering), | | |
| 2 | 2018-07-10T00:00:00 | Mandimby Ranaivo R. (AKKA), | | |
| 3 | 2018-08-02T00:00:00 | Eric Suignard (EDF), | | |
| 4 | 2018-09-21T00:00:00 | Eric Suignard (EDF), | | |
| 5 | 2018-10-04T00:00:00 | Eric Suignard (EDF), | Version post WP5&9 physical meeting in Tallinn | |
| 6 | 2018-10-17T00:00:00 | Eric Suignard (EDF), | Version reviewed by WP5&9 partners | |
| 7 | 2019-05-07T00:00:00 | Eric Suignard (EDF), | WP6-7-8 demos alignment and miscellaneous changes | |
| 8 | 2020-06-16T00:00:00 | Eric Suignard (EDF), | innogy’s and Elering’s review | |
1.3. Scope and Objectives of Use Case
| |
|---|
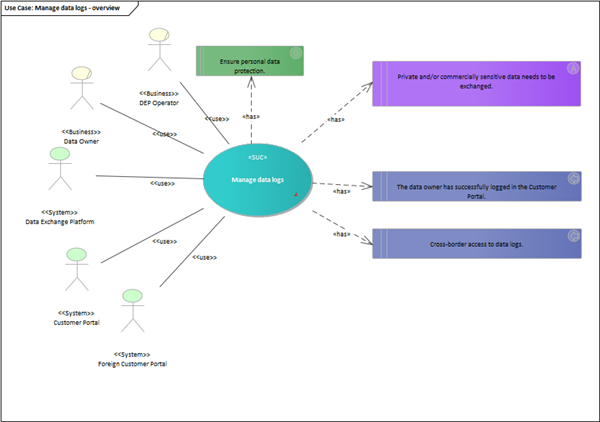
| Scope | Making available security logs including data access logs and authorization logs. |
| Objective(s) | Ensure personal data protection. |
| Related business case(s) | |
1.4. Narrative of Use Case
Short description
Data Owner’s access to data logs contributes to personal data protection. The data logs include information about data access (e.g. who has accessed consumption data and when), authorizations (e.g. who has issued a new authorization and when) and authentication (e.g. who has identified himself/herself in Customer Portal and when).
Complete description
Via a Customer Portal, a Data Owner (e.g. electricity consumer is the owner of its consumption data) has access to data logs. They include two types of logs:
- Data access logs: e.g. who has accessed data and when
- Authorization logs: e.g. who has requested/received authorization to access data and when
- Authentication logs: e.g. who has identified himself/herself in Customer Portal and when
The Customer Portal operator makes the data logs available in the Customer Portal. In addition, in case of cross border data exchange, the Customer Portal operators of the involved countries share information about data logs between them.
| ID | Name | Description | Reference to mentioned use case objectives |
|---|
1.6. Use case conditions
| Assumptions |
|---|
| Private and/or commercially sensitive data needs to be exchanged. |
| Prerequisites |
|---|
| The data owner has successfully logged in the Customer Portal. |
| Relation to other use cases |
|---|
|
| Level of depth |
| Prioritisation |
|
| Generic, regional or national relation |
|
| Nature of the use cases |
| SUC |
| Further keywords for classification |
|
2. Diagrams of Use Case
3. Technical Details
3.1. Actors
| Actor Name | Actor Type | Actor Description | Further information specific to this Use Case |
|---|
| Data Exchange Platform | System | Data exchange platform (DEP) is a communication platform the basic functionality of which is to secure data transfer (routing) from data providers (e.g. data hubs, flexibility service providers, TSOs, DSOs) to the data users (e.g. TSOs, DSOs, consumers, suppliers, energy service providers). DEP stores data related to its services (e.g. cryptographic hash of the data requested). The DEP does not store core energy data (e.g. meter data, grid data, market data) while these data can be stored by data hubs. Several DEPs may exist in different countries and inside one country. | |
| Foreign Customer Portal | System | Customer Portal for another country.
Can also mean a separate portal in the same country. | |
| Data Owner | Business | Any person who owns data and can give authorization to other parties to access them. Can be, inter alia:
- Flexibility Services Provider
- Market Operator
- Consumer
- Generator
| |
| Customer Portal | System | Customer Portal manages data users' authentication, access permissions and data logs. Customer Portals store data related to its services (e.g. authentication information, representation rights, access permissions, data logs). | |
| DEP Operator | Business | Data exchange platform operator owns and operates a communication system which basic functionality is data transfer. | |
3.2. References
| No. | References Type | Reference | Status | Impact on Use Case | Organistaor / Organisation | Link |
|---|
4. Step by Step Analysis of Use Case
4.1. Overview of Scenarios
| No. | Scenario Name | Scenario Description | Primary Actor | Triggering Event | Pre-Condition | Post-Condition |
|---|
| 1 | Data Owner accesses data logs | The Data Owner requests access to its data logs from the Customer Portal. In case of cross border data exchange, the later retrieves the data logs from the corresponding foreign Customer Portal. Finally, the Data Owner consults the requested data logs. | | | | |
Notes
4.2. Steps – Scenarios
| Scenario Name: |
|---|
| Data Owner accesses data logs |
| Step No. | Event. | Name of Process/ Activity | Description of Process/ Activity. | Service | Information Producer (Actor) | Information Receiver (Actor) | Information Exchanged | Requirements, R-ID |
|---|
| 1.1 | | Request data logs | The Data Owner requests data logs to the Customer Portal. The request contains the desired log type:
- Data access (e.g. who has accessed data and when)
- Authorization (e.g. who has requested/received authorization to access data and when)
- Authentication logs (e.g. who has identified himself/herself in Customer Portal and when)
It also contains selection criteria like dates, log level etc.
Modsarus Use Case::InstanceName=Data log request
Modsarus Use Case::InstanceDescription=
| | a17749ef-fb35-4331-9275-eaadfad82b36 | 5351ac19-9ec2-47b9-9ead-4a28907df045 baa61f8b-bde4-4008-820b-bfad5a7150f6 5351ac19-9ec2-47b9-9ead-4a28907df045 baa61f8b-bde4-4008-820b-bfad5a7150f6 | 2d790f31-c87f-4133-88ea-1a014cd10d9d | 2af6ad64-c90f-4bc9-aebd-7c01060f85c4 0b77ff6a-6c7b-4468-b248-a2a3be9b2916 8288215b-981b-464a-b352-195b019edec8 |
| 1.2 | | Retrieve data access logs | The Customer Portal retrieves data access logs corresponding to the received selection criteria.
Modsarus Use Case::InstanceName=Data access log
Modsarus Use Case::InstanceDescription=
| | baa61f8b-bde4-4008-820b-bfad5a7150f6 | a17749ef-fb35-4331-9275-eaadfad82b36 | b1d9b26e-8b21-4225-88c3-bc86a46a851e | 2af6ad64-c90f-4bc9-aebd-7c01060f85c4 0b77ff6a-6c7b-4468-b248-a2a3be9b2916 8288215b-981b-464a-b352-195b019edec8 |
| 1.3 | | Retrieve authorization logs | The Customer Portal retrieves authorization logs corresponding to the received selection criteria.
Modsarus Use Case::InstanceName=Authorization request log
Modsarus Use Case::InstanceDescription=
| | baa61f8b-bde4-4008-820b-bfad5a7150f6 | a17749ef-fb35-4331-9275-eaadfad82b36 | b1d9b26e-8b21-4225-88c3-bc86a46a851e | 2af6ad64-c90f-4bc9-aebd-7c01060f85c4 0b77ff6a-6c7b-4468-b248-a2a3be9b2916 8288215b-981b-464a-b352-195b019edec8 |
| 1.4 | | Retrieve data access logs | The foreign Customer Portal retrieves data access logs corresponding to the received selection criteria and hands them over to the original Customer Portal.
Modsarus Use Case::InstanceName=Data access log
Modsarus Use Case::InstanceDescription=
| | 5351ac19-9ec2-47b9-9ead-4a28907df045 | baa61f8b-bde4-4008-820b-bfad5a7150f6 | b1d9b26e-8b21-4225-88c3-bc86a46a851e | 2af6ad64-c90f-4bc9-aebd-7c01060f85c4 0b77ff6a-6c7b-4468-b248-a2a3be9b2916 8288215b-981b-464a-b352-195b019edec8 |
| 1.5 | | Retrieve authorization logs | The foreign Customer Portal retrieves authorization request logs corresponding to the received selection criteria and hands them over to the original Customer Portal.
Modsarus Use Case::InstanceName=Authorization request log
Modsarus Use Case::InstanceDescription=
| | 5351ac19-9ec2-47b9-9ead-4a28907df045 | baa61f8b-bde4-4008-820b-bfad5a7150f6 | b1d9b26e-8b21-4225-88c3-bc86a46a851e | 2af6ad64-c90f-4bc9-aebd-7c01060f85c4 0b77ff6a-6c7b-4468-b248-a2a3be9b2916 8288215b-981b-464a-b352-195b019edec8 |
| 1.6 | | Consult data logs | The Data Owner receives the data log records he requested. | | a17749ef-fb35-4331-9275-eaadfad82b36 | | | 2af6ad64-c90f-4bc9-aebd-7c01060f85c4 0b77ff6a-6c7b-4468-b248-a2a3be9b2916 8288215b-981b-464a-b352-195b019edec8 |
| Information exchanged ID | Name of Information | Description of Information Exchanged | Requirement |
|---|
| 2d790f31-c87f-4133-88ea-1a014cd10d9d | Data log request | Contains the type of the requested logs (data access logs or authorization request logs) and other criteria like dates, log level etc. | —- |
| b1d9b26e-8b21-4225-88c3-bc86a46a851e | Data log | Contains the selected log records. | —- |
6. Requirements (optional)
| Category Identifier | Name | Description | mRID |
|---|
| Cat1 | Personal data | | bd1580a2-20b8-41fa-a8df-2ae6041bf604 |
| Identifier | Name | Description | mRID |
|---|
| Req1 | Access Citizen Right | Right to secure direct access of own personal data and to any processing, storage or sharing details | 2af6ad64-c90f-4bc9-aebd-7c01060f85c4 |
| Req2 | Informed Citizen Right | Right to be informed of any personal data held, of how it is used or processed, of any breach, and of any disclosure/usage to third parties | 0b77ff6a-6c7b-4468-b248-a2a3be9b2916 |
| Category Identifier | Name | Description | mRID |
|---|
| Cat2 | Task 5.3 | Requirements integrated from Task 5.3. | 1880e39c-7084-4785-8c02-297057abe312 |
| Identifier | Name | Description | mRID |
|---|
| Req3 | LOGS-REQ1 | Ability to share information related to data logs between data owners, concerned DEPs, applications and data sources | 8288215b-981b-464a-b352-195b019edec8 |
7. Common Terms and Definitions
| Key | Value | Refers to Section |
|---|

